Chrome extensions are incredibly useful, whether you want to block ads, track the best deals or enhance your browsing experience. They can be downloaded from the Chrome Web Store, which functions like the Play Store but for extensions. However, extensions are easier to mimic and turn into malicious software compared to apps.
As we just reported, over 3.2 million users were victimized by a security breach tied to 16 malicious browser extensions, highlighting how attackers exploit tools that seem legitimate to spread malware or steal sensitive data.
Now, security researchers have discovered a polymorphic attack that allows malicious Chrome extensions to transform into other browser extensions, including password managers, crypto wallets and banking apps, to steal sensitive information.
Keep reading to learn how this attack works and how to protect yourself from it.
STAY PROTECTED & INFORMED! GET SECURITY ALERTS & EXPERT TECH TIPS – SIGN UP FOR KURT’S THE CYBERGUY REPORT NOW
How the malicious polymorphic attack works
Security researchers at SquareX Labs have found a new attack that lets malicious Chrome extensions disguise themselves as legitimate ones, like password managers, crypto wallets and banking apps, to steal sensitive information. This “polymorphic” attack takes advantage of Chrome’s extension system to trick users while staying under the radar.
The attack starts with hackers uploading what looks like a harmless extension to the Chrome Web Store. It might even have real features, like an AI-powered marketing tool, to convince users to install and pin it to their browser.
Once installed, the malicious extension scans the victim’s browser for other extensions. It can do this in two ways. If it has permission to use the “chrome.management” API, it grabs a list of installed extensions directly. If not, it injects code into web pages to check for unique files or resources tied to certain extensions.
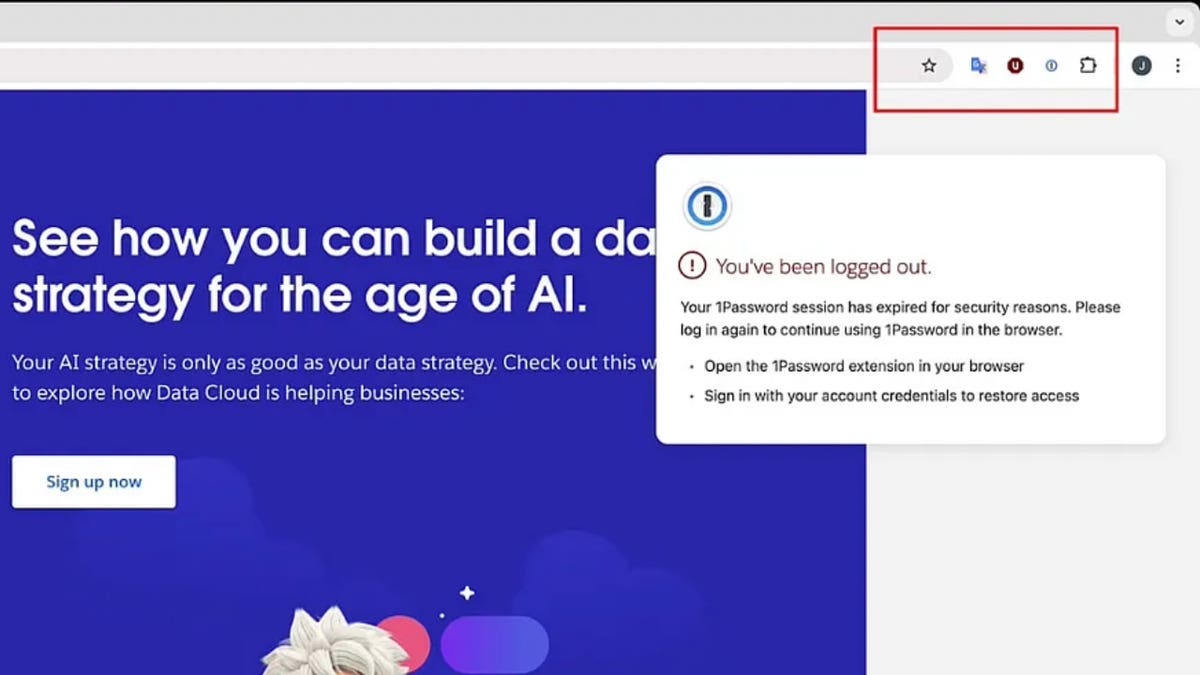
If it finds a targeted extension, like 1Password, the malicious extension reports back to an attacker-controlled server. The attacker then tells it to impersonate the real extension by disabling it if permissions allow, changing its name and icon and displaying a fake login popup that looks just like the real thing.
THE HIDDEN COSTS OF FREE APPS: YOUR PERSONAL INFORMATION
Social engineering makes things worse
To steal user credentials, the malicious extension triggers a fake “Session Expired” prompt when the victim tries to log in to a website. This tricks them into thinking they need to reenter their credentials for their password manager or banking app. When they do, the stolen data is sent straight to the attackers.
After collecting the credentials, the extension switches back to its original form. It restores the legitimate extension, making everything look normal so the victim doesn’t suspect anything. This shows just how dangerous malicious Chrome extensions can be and why stronger security measures are needed to protect users.
We reached out to Google, and a spokesperson told CyberGuy, “We appreciate the work of the research community and we’ve received the report. We are constantly investing in ways to improve the security of the Chrome Web Store, and we take appropriate action when we learn of emerging threats.”
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?

OUTSMART HACKERS WHO ARE OUT TO STEAL YOUR IDENTITY
5 ways you can protect your personal data
Here are five ways to safeguard your sensitive information and maintain your online privacy.
1. Keep your browser and extensions up to date: Outdated software is a goldmine for cybercriminals. Bugs or security gaps in old versions of your browser or extensions can be exploited to inject malicious code, steal data or take control of your system. Updates patch these vulnerabilities, making them a critical line of defense. Turn on automatic updates for your browser (e.g., Chrome, Firefox, Edge) so you’re always running the latest version without thinking about it. See my guide on keeping your devices and apps updated for more information.
2. Install extensions only from trusted sources: Official browser stores like the Chrome Web Store or Firefox Add-ons have rules and scans to catch bad actors, but they’re not perfect. Extensions from random websites or third-party downloads are far more likely to hide malware or spyware. Stick to the official store for your browser; don’t download extensions from sketchy links.
3. Have strong antivirus software: The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
4. Update your passwords: Change passwords for any accounts that may have been affected by the extension and use unique, strong passwords for each account. Consider using a password manager. This can help you generate and store strong, unique passwords for all your accounts. Get more details about my best expert-reviewed password managers of 2025 here.
5. Invest in personal data removal services: If your personal data gets stolen by the extension, it’s crucial to act quickly to reduce your risk of identity theft and scams. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
MASSIVE SECURITY FLAW PUTS MOST POPULAR BROWSERS AT RISK ON MAC
Kurt’s key takeaway
The malicious extension highlights that Google isn’t doing enough to keep malware off its platform. Security researchers pointed out that the Chrome Web Store lacks protections against these types of attacks, such as blocking sudden changes to an extension’s icon or HTML, or at least alerting users when such changes occur. The problem isn’t limited to the Chrome Web Store. The Play Store also hosts malicious apps from time to time, affecting millions of users. Google needs to step up its security efforts and put user privacy front and center.
Do you trust Google to keep malicious apps and extensions off its platforms? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most-asked CyberGuy questions:
New from Kurt:
Copyright 2025 CyberGuy.com. All rights reserved.
Read the full article here










